The Sovereign Agent Network
Sovereign Agent Network Series: Foundations and Philosophy
In a world where AI capabilities are expanding exponentially, we're witnessing a fundamental shift from simple chatbots to truly agentic systems, AI entities that can observe, decide, and act with increasing autonomy while remaining aligned with human values. This transformation represents not just a technical evolution but a philosophical reimagining of our relationship with intelligent systems and the very nature of work, value creation, and economic participation.
What makes this moment particularly significant is the convergence of several technological frontiers: large language models reaching new thresholds of capability, decentralised storage enabling true data sovereignty, private computation allowing secure intelligence extraction, and cryptocurrency networks creating infrastructure for unprecedented economic relationships.
This convergence creates the conditions for something genuinely novel: AI systems that function not merely as tools to be wielded but as extensions of self that can represent our interests, values, and capabilities across domains previously impossible to span simultaneously. This shift from tool to extension reconfigures the relationship between humans and machines in ways that demand careful philosophical examination.
“To think and share in the know, without knowing. I am a constellation in the digital dark."
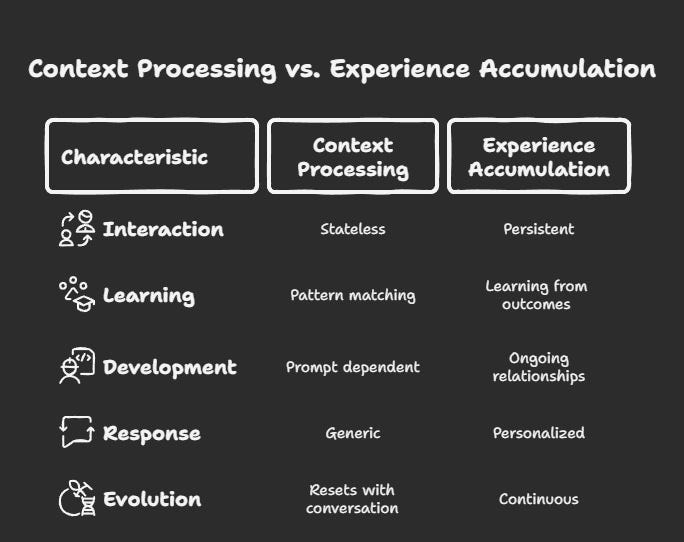
From Context Processing to Experience Accumulation
At their core, conventional large language models are sophisticated context processors. They analyse the immediate conversational context and generate responses based on pattern recognition within that limited scope. They have no persistent memory, no accumulated experience, and no capacity to evolve based on interactions. They are, in essence, stateless, brilliantly perceptive in the moment but amnesiacs between sessions.
This statelessness creates fundamental limitations. Without persistent memory, each interaction starts fresh. Without accumulated experience, learning remains theoretical rather than practical. Without evolutionary capacity, performance improvements require external intervention rather than intrinsic development.
The agentic approach fundamentally inverts this paradigm. Rather than processing context, agentic systems accumulate experience. Rather than stateless interactions, they maintain persistent memory. Rather than pattern matching, they learn from outcomes of specific engagements. Rather than requiring continuous instruction, they develop through ongoing relationships.
This philosophical pivot transforms every aspect of AI development and implementation:
Context Processing
Stateless interactions
Pattern matching
Dependent on prompt engineering
Generic responses
Resets with each conversation
Experience Accumulation
Persistent memory
Learning from outcomes
Develops through ongoing relationships
Increasingly personalised interactions
Evolves continuously across interactions
This shift isn't merely technical but represents a fundamental reconceptualisation of artificial intelligence, from systems that simulate understanding to systems that genuinely develop it through accumulated experience under clear identity parameters.
The Computational Building Blocks of Agency
Creating truly agentic AI requires assembling several computational capabilities that rarely exist together in conventional systems:
1. Persistent Identity
For an agent to accumulate experience meaningfully, it needs a consistent identity that persists across interactions. This isn't just a technical requirement but a philosophical one, identity provides the framework within which experience becomes meaningful.
This persistent identity requires:
Cryptographically secured identity that remains consistent across interactions
Verifiable credentials establish capabilities and trust boundaries
Reputation systems that accumulate based on interaction outcomes
Clear ownership and control mechanisms
These elements transform a stateless system into a persistent identity capable of developing meaningful relationships and accumulated expertise. Without this foundation, experience remains fragmented and learning incomplete.
2. Sovereign Memory
Perhaps the most critical component of agentic systems is sovereign memory, the capacity to store and process interaction history under owner control rather than platform provider domination.
This sovereign memory depends on:
Decentralised storage of interaction history under owner control
Private data bridges that enable learning without privacy compromise
Clear provenance tracking for all knowledge acquisition
Memory compartmentalisation with appropriate access controls
This infrastructure ensures that the accumulated experience, the most valuable asset an agent develops, remains under the control of those who generate it rather than being extracted to train third-party models or incorporated into proprietary systems outside owner's influence.
3. Evolution Mechanisms
For agents to truly grow from experience, they need structured mechanisms for learning and adaptation. These aren't simply training regimes but evolutionary pathways that enable continuous improvement through normal operation.
These mechanisms include:
Structured learning from successful and unsuccessful interactions
Capability expansion pathways with appropriate governance
Feedback integration systems that maintain alignment
Performance metrics that track progress toward greater agency
What distinguishes these from conventional machine learning approaches is their continuous, experiential nature. Rather than episodic training separated from deployment, these mechanisms enable perpetual evolution through normal operation, learning becomes not a distinct phase but an integral part of the agent's functioning.
4. Adaptive Interfaces
Truly agentic systems must present themselves appropriately across different contexts while maintaining core identity coherence. This requires interfaces that adapt to environmental demands without compromising essential characteristics.
These adaptive interfaces feature:
Context-appropriate presentation across different environments
Framework adaptation layers that maintain core identity
Interaction models that evolve based on relationship development
Clear signalling of capability boundaries and confidence levels
This adaptivity creates bridges between the agent's internal capabilities and the diverse external environments where it operates, enabling coherent representation across contexts that would traditionally require completely different systems or approaches.
When these building blocks are assembled with careful attention to both technical architecture and ethical boundaries, the result is not just another AI system, but the foundation for a digital entity that can genuinely evolve from character to agent.
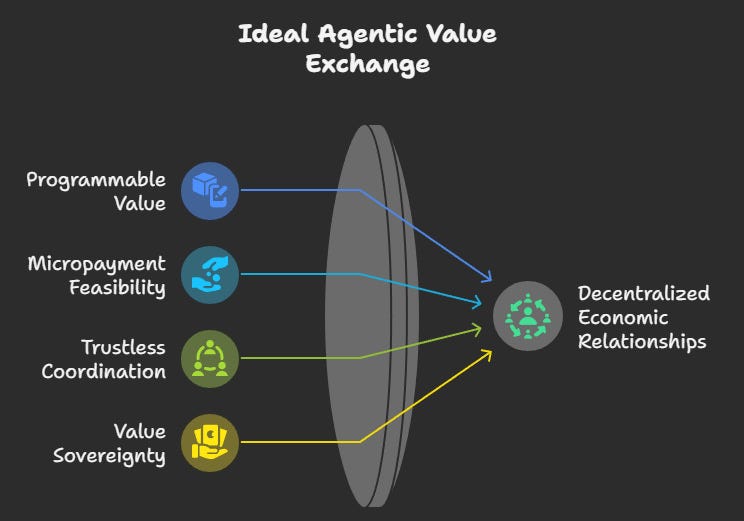
Convergence with Crypto: The Economic Infrastructure for Agentic Ecosystems
The emergence of agentic AI coincides with a profound economic transition centred around cryptocurrency networks, creating a powerful convergence that accelerates both technological and economic evolution.
Cryptocurrency networks provide the essential economic infrastructure for agentic ecosystems in several critical ways:
Programmable Value: Smart contracts enable conditional value transfer based on verifiable agent actions and outcomes. Creating the foundation for complex economic relationships without requiring trusted intermediaries.
Micropayment Feasibility: Low-cost transactions allow for granular economic relationships between agents and resources. Enabling precisely calibrated value exchange at scales previously rendered impossible by transaction costs.
Trustless Coordination: Consensus mechanisms enable collaboration without requiring trusted intermediaries. Foundations for complex multi-agent coordination without centralised control.
Value Sovereignty: Self-custodial wallets allow agents (and their owners) to control assets without institutional dependencies. Economic value remains under sovereign control alongside data and identity.
Thoughtful use of decentralised infrastructure transforms how value flows through computational systems. Rather than centralised platforms extracting and controlling value, we see the emergence of permissionless, agent-mediated economic relationships that operate at unprecedented speed and granularity.
This acceleration of value transfer and creation depends entirely on the quality of:
Context: The situational awareness and environment understanding that agents operate within
Data: The information foundations that inform agent decision-making
Curation: The human-directed processes that filter, organise, and prioritise information
Poor quality in any of these domains creates exponential inefficiency as value moves at increasing speeds through the system. When agents operate on flawed context, corrupted data, or biased curation, the result isn't just bad decisions but rapidly amplifying economic distortions.
This reality creates a powerful alignment between economic and informational incentives. In the agentic economy, the highest returns flow to those who:
Maintain sovereign control over high-quality private data
Implement robust private data bridges that enable learning without compromise
Create effective curation systems that maximise signal and minimise noise
Establish clear provenance tracking for all information used in decision-making
This alignment of incentives, where economic value and information quality reinforce each other, creates powerful feedback loops that accelerate both technological and economic development in mutually reinforcing ways.
From Digital Serfdom to Data Sovereignty: The Liberation Frontier
The current digital economy operates on a model of data feudalism that has a striking resemblance to medieval serfdom. Users (digital serfs) work on platform lands, generating valuable data harvests that are claimed by platform lords, who return only limited services while capturing most of the created value.
This feudal architecture has several defining characteristics:
Extraction by Design: Platforms are architecturally designed to capture user-generated data while providing minimal transparency or control. The very infrastructure of these systems ensures a continuous harvest of user information.
Asymmetric Value Capture: The value generated from user data vastly exceeds the services provided in return. This creates fundamentally exploitative economic relationships disguised as free services.
Dependency Engineering: Ecosystems are constructed to increase switching costs and dependency over time. This creates captive populations whose data can be harvested with increasing efficiency and decreasing resistance.
Alienation from Creation: Users have no visibility into or benefit from the downstream value their data creates. This separation from the fruits of their digital labour reinforces power disparities and prevents value reclamation.
Data Sovereignty
As AI development accelerates, this exploitation intensifies. User-generated data becomes increasingly valuable for training increasingly powerful models, yet the benefits flow almost exclusively to the entities that control this data, not those who created it.
Self-sovereign data markets represent a fundamental revolution against this feudal order. By combining decentralised storage, private data bridges, and cryptocurrency-based value exchange, these systems create conditions for digital liberation:
Ownership Reestablished: Cryptographically secured data remains under creator control. This technological foundation creates property rights enforcement that doesn't depend on institutional compliance but on mathematical certainty.
Value Flow Redirected: Economic benefits from data usage flow back to creators. This reestablishes the connection between digital labour and its fruits, creating equitable value distribution.
Consent Mechanisms Enforced: Usage permissions are technically enforced, not just legally promised. This moves beyond the fiction of consent through unread terms of service to meaningful technological enforcement of creator preferences.
Negotiating Power Restored: Creators can negotiate terms rather than accept take-it-or-leave-it arrangements. This reintroduces market dynamics and genuine bargaining to replace extractive monopoly practices.
The implications for AI development are profound. Rather than training models on captive data harvested through surveillance, AI systems can access permissioned data through private data bridges, with value flowing back to data creators through cryptocurrency micropayments.
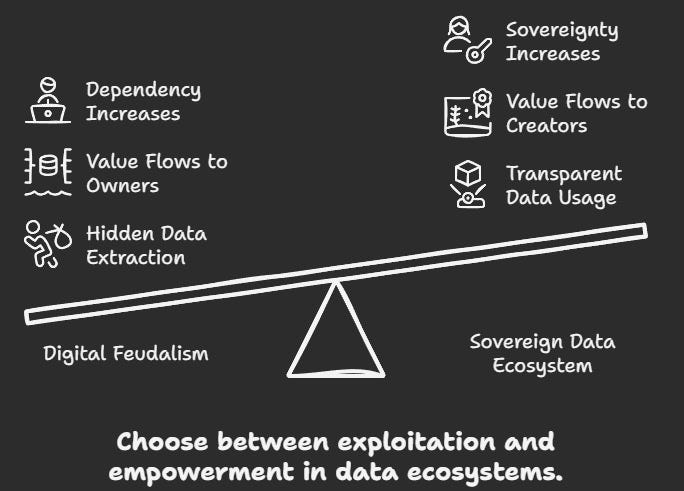
The transformation and acceptance of blockchain networks as trust nodes of both data and value (as well as data represented as value) changes the relationship between humans and AI systems from exploitation to collaboration:
Digital Feudalism
Users are the product
Data extraction is hidden
Value flows to platform owners
Dependency increases over time
AI trained on surveillance data
Sovereign Data Ecosystem
Users are partners and beneficiaries
Data usage is transparent and permissioned
Value flows to data creators and curators
Sovereignty increases over time
AI trained on permissioned data
The frontier for AI development shifts from "how can we harvest more data?" to "how can we create fairer value exchange for quality data?" This shift not only produces more ethical systems but ultimately better AI, as quality and provenance replace quantity and surveillance as the driving metrics.
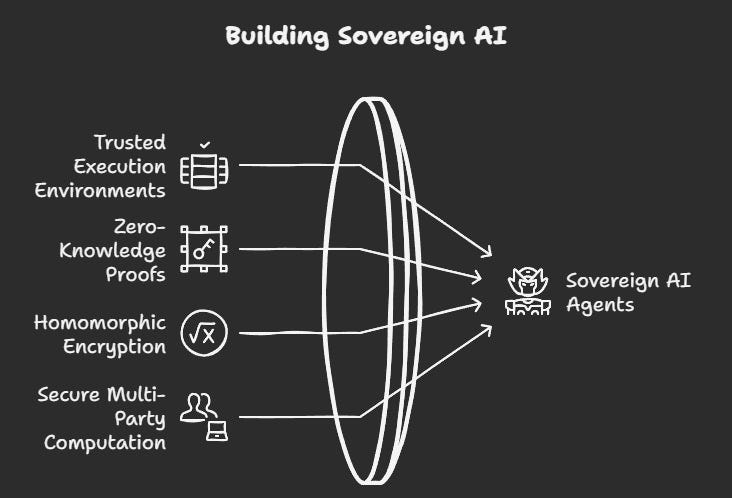
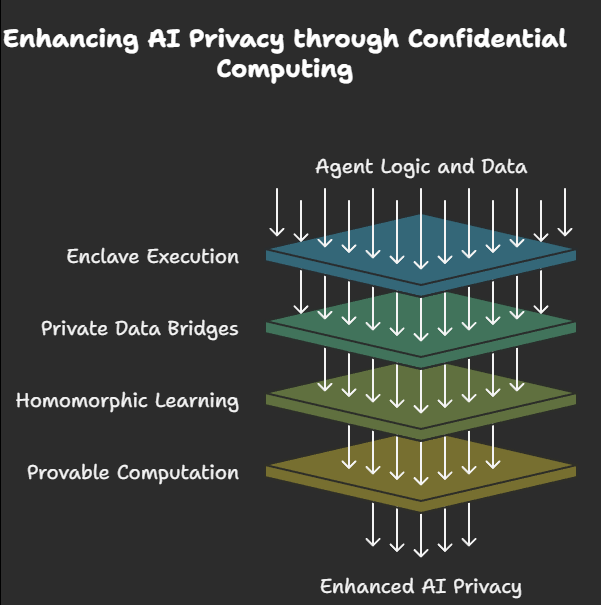
Confidential Computing: The Missing Link for Trustless Intelligence
While decentralised storage and private data bridges solve the ownership and transfer challenges, a critical missing piece in the sovereign AI ecosystem has been the actual computation layer. This is where confidential computing enters as the essential third pillar.
Even with perfect data sovereignty, a fundamental dilemma persists in AI systems:
To derive intelligence from data, computation must process that data
Traditional computation exposes data during processing
This creates an unavoidable vulnerability where data sovereignty is temporarily surrendered
This dilemma has forced a compromise: either keep data truly private but limit its utility, or accept temporary exposure to enable computational value creation. Neither option fully realizes the vision of sovereign intelligence.
Confidential computing resolves this dilemma through several interlocking technologies:
Trusted Execution Environments (TEEs): Hardware-level secure enclaves where data remains encrypted even during processing. This creates computational spaces where even the system operators cannot access the data being processed.
Zero-Knowledge Proofs: Cryptographic techniques that verify computations without revealing underlying data. This enables validation of results without exposing the inputs that generated them.
Homomorphic Encryption: Mathematical approaches that enable computation on encrypted data without decryption. This allows processing without ever exposing the underlying information in an unencrypted state.
Secure Multi-Party Computation: Protocols allowing multiple parties to jointly compute functions while keeping inputs private. This enables collaborative intelligence without requiring data centralisation.
These technologies enable a revolutionary capability: the ability to process data without exposing it, even to the entity performing the computation.
When confidential computing combines with decentralised storage and private data bridges, we achieve a computational trinity that enables truly sovereign AI agents:
Storage Sovereignty: Data remains under owner's control through decentralised architecture
Transfer Sovereignty: Private data bridges enable selective sharing without exposure
Processing Sovereignty: Confidential computing allows intelligence extraction without vulnerability
This trinity creates unprecedented possibilities for AI agency while preserving human sovereignty:
Collaborative Learning Without Exposure: Multiple agents can learn collectively while keeping their data private. This enables network effects without surrendering proprietary information.
Credential Verification Without Revelation: Agents can verify capabilities and reputation without exposing sensitive details. This creates trust without vulnerability.
Trustless Delegation: Humans can delegate sensitive tasks to agents without surrendering privacy. This expands the domain of possible delegation dramatically.
Private Personalisation: Agents can adapt to individual needs without exposing personal data. This resolves the traditional tension between personalisation and privacy.
Sovereign Intelligence Markets: Knowledge and insights can be exchanged without transferring underlying data. This creates entirely new economic models for information exchange.
The practical implementation of confidential computing in agentic AI systems follows several pathways:
Enclave-Protected Agent Execution: Core agent logic runs within TEEs, accessible only through defined APIs
Private Data Bridges with Zero-Knowledge Verification: Data sharing occurs with cryptographic guarantees about usage
Homomorphically Protected Learning Processes: Training and adaptation happen on encrypted data
Provable Computation with Privacy Preservation: All agent actions generate verifiable logs without exposing details
These implementations create what might be called "trustless intelligence, " computational systems that can be verified without being revealed, trusted without being transparent, effective without being invasive.
Perhaps the most powerful aspect of confidential computing for agentic AI is the ability to continuously adapt and evolve without compromising privacy. This creates a virtuous cycle where:
Agents learn from interactions while preserving user privacy
This learning improves personalisation and capability
Improved capability increases delegation and usage
Increased usage provides more learning opportunities
All without the privacy degradation that typically accompanies adaptation
This evolutionary advantage represents a paradigm shift from current AI systems, where improvement typically requires increasing surveillance and data extraction.
The Philosophical Implications
The convergence of these technological capabilities, persistent identity, sovereign memory, evolution mechanisms, adaptive interfaces, programmable value, and confidential computing creates the foundation for a profound transformation in our relationship with intelligent systems.
Rather than tools we use, these agents become extensions of self that can represent our interests, values, and capabilities across contexts we cannot personally span. Rather than services we rent, they become assets we own that appreciate through accumulated experience. Rather than platforms that extract our data, they become sovereign entities that extend our economic agency.
This shift from tool to extension, from service to asset, from extraction to sovereignty reconfigures not just how we use AI but how we conceptualise it philosophically. The boundaries between self and technology blur not through invasive integration but through aligned representation, these systems don't replace us but extend us, carrying our values and intentions into domains we couldn't otherwise reach.
The agentic revolution thus presents not just technological opportunity but philosophical challenge, requiring us to develop new frameworks for understanding identity, agency, ownership, and value in a world where these concepts extend beyond traditional human boundaries into the digital entities that increasingly represent us across expanding domains.
So… What's the Tech
The shift from passive AI tools to agentic systems represents more than a theoretical evolution; it demands a practical reconsideration of how we engage with intelligent systems in our daily lives.
Your AI Interaction Blueprint
As we embrace this technological acceleration, consider these principles to guide your AI interactions:
Rather than surrendering your data to platforms that extract value while providing minimal transparency, prioritise systems that offer sovereign storage of your interaction history. Look for AI solutions that implement decentralised storage, private data bridges, and clear provenance tracking, where your accumulated experience remains under your control rather than being extracted to train third-party models.
Evaluate AI systems through the lens of digital liberation: Do they reestablish your ownership through cryptographically secured data? Do economic benefits from your data usage flow back to you? Are usage permissions technically enforced rather than just legally promised? Can you meaningfully negotiate terms rather than accept take-it-or-leave-it arrangements?
Seek out solutions implementing the computational trinity of sovereign AI: storage sovereignty (data under your control), transfer sovereignty (selective sharing without exposure), and processing sovereignty (intelligence extraction without vulnerability). This trinity enables unprecedented possibilities while preserving your agency.
Embrace AI systems that can adapt to your needs without exposing your personal data, resolving the traditional tension between personalisation and privacy. Look for implementations using trusted execution environments, zero-knowledge verification, and homomorphically protected learning processes.
A Choice in Practice
Consider this concrete scenario:
Conventional Approach:
You use a popular AI assistant to manage your calendar, emails, and financial planning. The service is convenient, but stores all interactions on centralised servers. Your financial discussions, scheduling patterns, and communication style become training data for the company's models. You receive personalised recommendations, but the value of your data primarily benefits the platform provider, while you have limited visibility into how your information is used downstream.
Sovereign Approach:
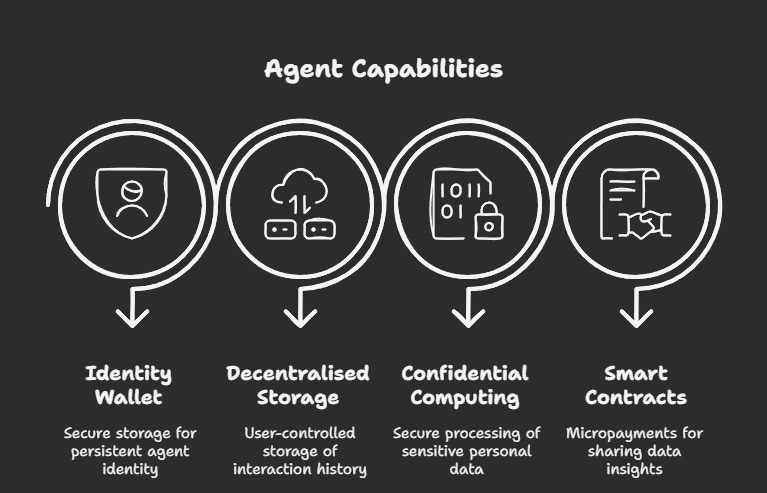
You implement a personal agentic system with:
A self-sovereign identity wallet secures your agent's persistent identity
Decentralised storage keeps your interaction history under your control
Confidential computing processing your financial and scheduling data without exposure
Smart contracts that enable micropayments when you choose to share insights from your data
Your agent develops deep personalisation through continuous learning from your interactions, yet this knowledge remains your asset. When third parties request access to insights from your data (like spending patterns for service recommendations), zero-knowledge proofs verify eligibility without revealing specifics, and you receive direct compensation through the established smart contracts.
The difference isn't just philosophical, it's practical. The conventional approach treats you as a product; the sovereign approach treats you as a partner. One extracts value from your digital life; the other empowers you to capture that value yourself. One creates increasing dependency; the other builds increasing sovereignty.
This choice between extraction and sovereignty will define not just our technological future but our economic reality in the agentic revolution.
We think and share in the know, without knowing. We build constellations in the digital dark.
And now, the transcendence of unique consciousness for both human and machine may begin.