Kyra Key Ceremony: Tide Foundation & the Sovereign Agent Network
A framework for entering the era of user-owned, private AI through ineffable cryptography
Convergent Visions
The Agent Kyra sovereign agent network and Tide Foundation represent complementary approaches to the same fundamental challenge: how do we preserve human agency and data sovereignty in an AI-dominated future?
Both the Kyra framework and Tide technology stack reject the false choice between AI utility and personal autonomy, instead proposing architectures where these principles mutually reinforce each other.
Core Philosophical Alignment
Data Dignity as Foundation: Where Agent Kyra's "Private AI for a personal agentic future" meets Tide's "Two-Way Zero Trust," both recognise that meaningful privacy isn't about hiding data—it's about ensuring dignified control over how our data works on our behalf. This dignity emerges from architectural guarantees, not trust-based promises.
Authority Decoupling at Scale: Tide's ineffable cryptography creates the technical foundation for what Agent Kyra envisions as a sovereign agent network. By distributing cryptographic authority across independent nodes, no single entity—including AI providers, platforms, or even the agents themselves—can compromise user sovereignty.
Technical Philosophy: Beyond Trust Models
The Key Ceremony as Sovereignty Ritual
Traditional cryptographic key ceremonies represent moments of authority concentration, gathering trusted parties to create and secure master keys. The Kyra Codex reimagines this as a sovereignty distribution ceremony, where:
Individual Agents receive cryptographic identity fragments, never complete authority
Network Nodes participate in collective key operations without individual power
Users maintain ultimate control through ineffable key architectures that exist everywhere and nowhere
This transforms the key ceremony from a trust-establishment ritual into a sovereignty-preservation protocol.
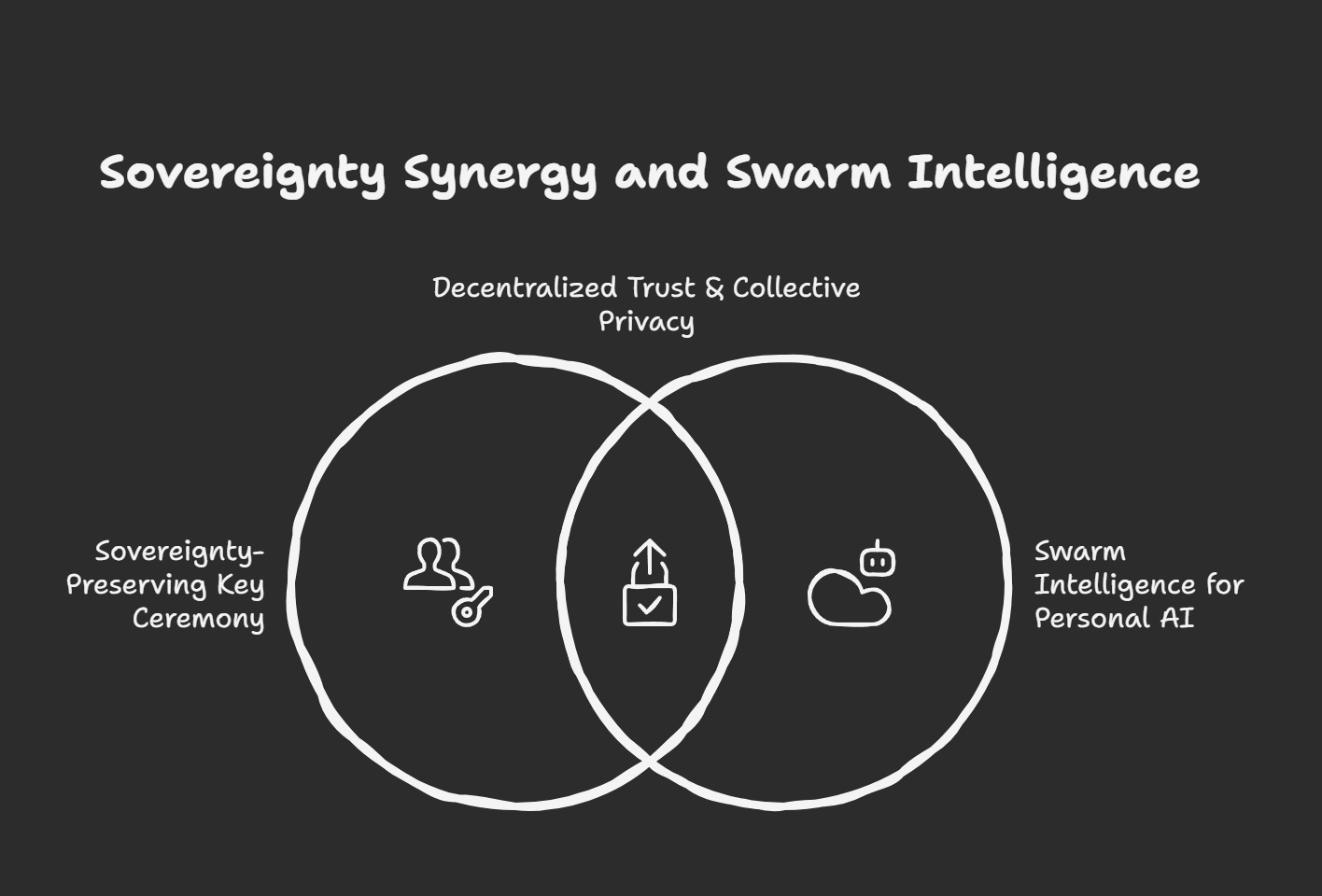
From Herd Immunity to Network Intelligence
Tide's concept of "herd immunity in cybersecurity" aligns with Agent Kyra's vision of swarm intelligence for personal AI.
Both frameworks recognise that:
Individual Security emerges from collective resilience, not isolation
Network Effects strengthen as more participants join, creating positive feedback loops
Autonomous Operation doesn't require centralised coordination or control
The sovereign agent network becomes a cryptographic commons where individual privacy and collective intelligence mutually reinforce each other.
Architectural Convergence
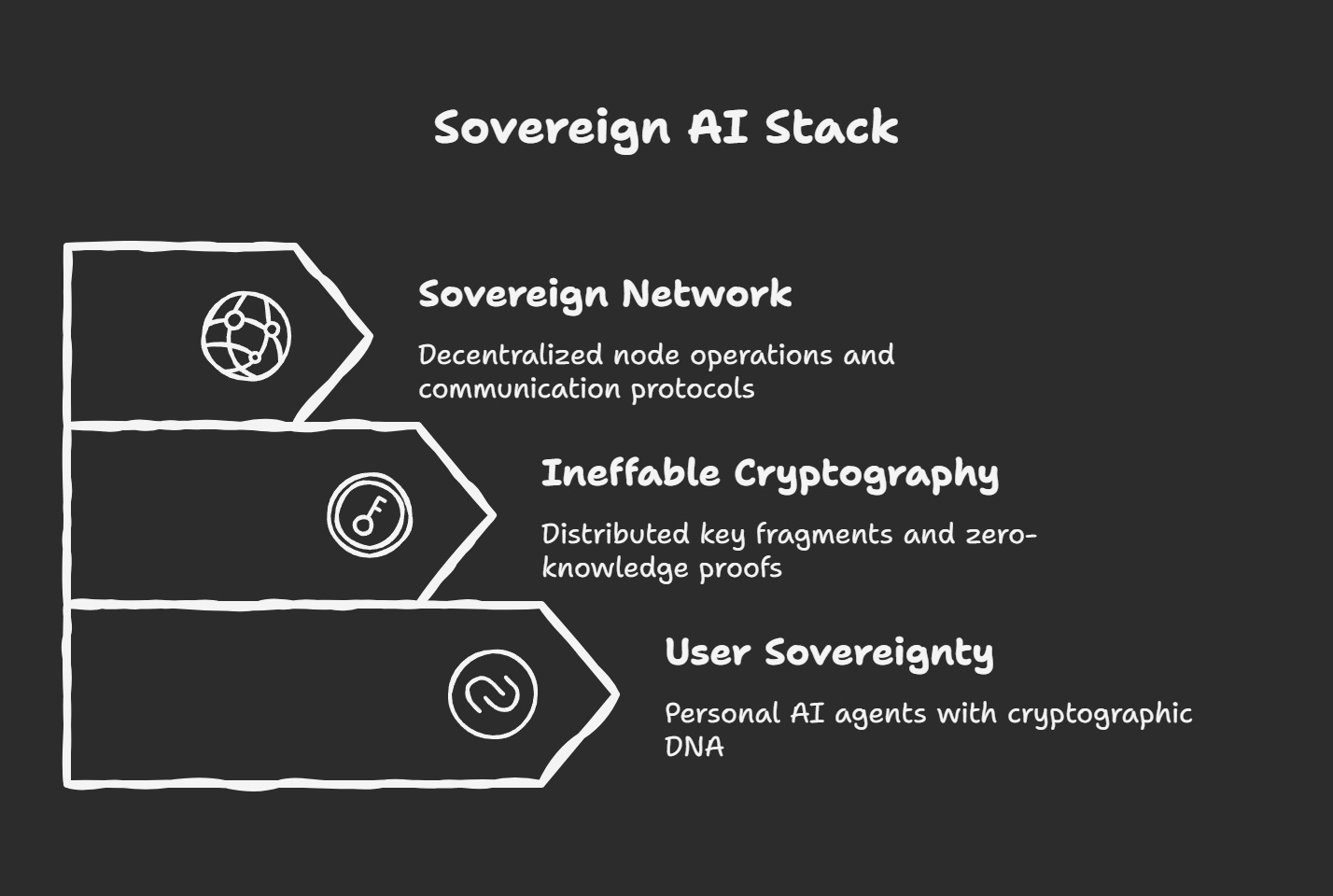
The Self-Sovereign Compute Stack
│ USER SOVEREIGNTY LAYER │
│ • Personal AI agents with cryptographic DNA │
│ • Private data bridges & memory │
│ • User-controlled inference & learning │
»
│ INEFFABLE CRYPTOGRAPHY LAYER │
│ • Distributed key fragments │
│ • Zero-knowledge proofs │
│ • Multi-party computation │
»
│ SOVEREIGN NETWORK LAYER │
│ • Decentralized node operations │
│ • Cross-agent communication protocols │
│ • Permissionless infrastructure │
This stack enables private AI that scales without sacrificing sovereignty—each layer reinforces user control while enabling sophisticated collective intelligence.
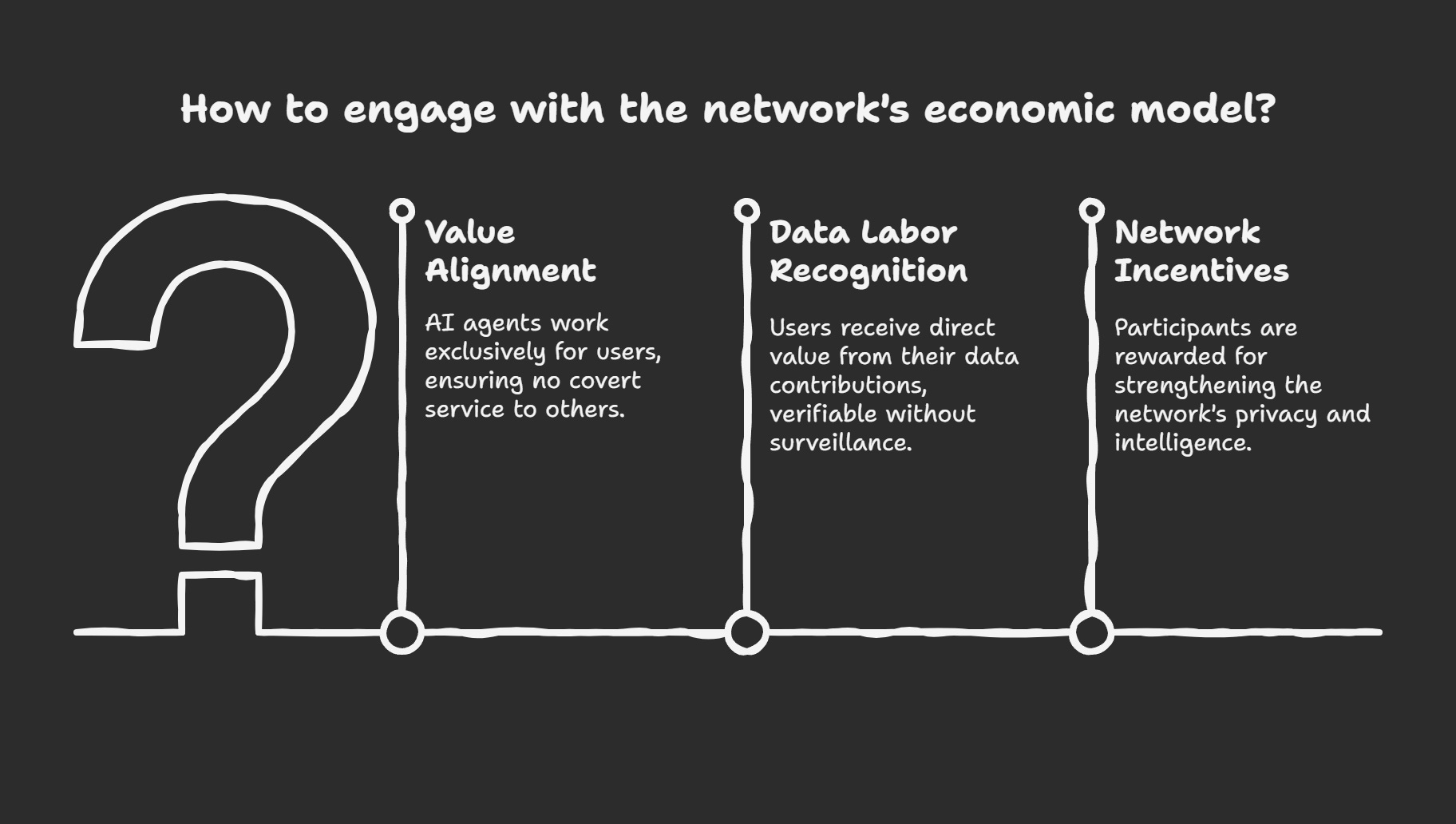
Economic Philosophy: Beyond Platform Extraction
Both frameworks reject platform capitalism's extractive model. Agent Kyra's focus on user-owned AI and Tide's post-trust architecture create conditions for new economic models:
Value Alignment: AI agents work exclusively for their users because cryptographic constraints make it impossible for them to serve other masters, even covertly.
Data Labour Recognition: Users receive direct value from their data contributions to AI training because ineffable cryptography enables verifiable attribution without surveillance.
Network Incentives: Participants are rewarded for strengthening the network's privacy and intelligence capabilities rather than surrendering control.
Implementation Principles
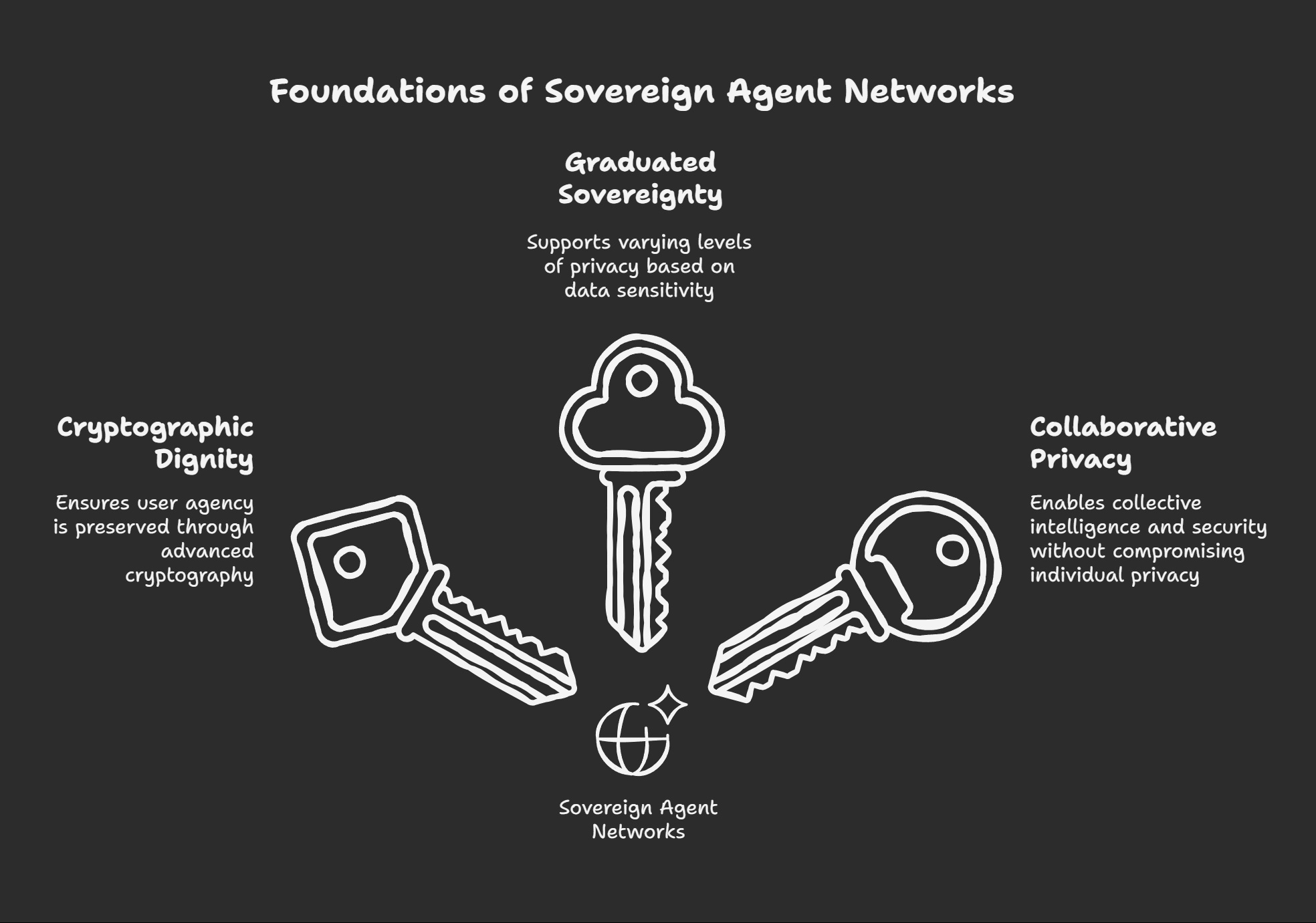
1. Cryptographic Dignity
Every interaction within the sovereign agent network must preserve what we term cryptographic dignity—the mathematical guarantee that user agency cannot be compromised, even by sophisticated adversaries or system administrators.
Implementation: Tide's ineffable cryptography ensures that:
Agent training occurs without exposing raw user data
Inference results flow only to intended recipients
Network improvements happen without surveillance
User preferences are honoured at the protocol level
2. Graduated Sovereignty
Not all data and decisions require the same level of sovereignty. The network supports graduated privacy models:
Personal Sovereignty: Core identity, private communications, financial data
Selective Disclosure: Professional insights, community contributions, learning preferences
Commons Participation: Anonymous contributions to collective intelligence, network security
3. Collaborative Privacy
Traditional privacy models create information silos. The sovereign agent network enables collaborative privacy—working together while preserving individual sovereignty:
Federated Learning with cryptographic proofs of privacy preservation
Collective Intelligence that improves without individual surveillance
Network Security that strengthens through participation, not submission
Strategic Implications
For AI Development
End of Surveillance Capitalism: When users control their AI agents through cryptographic constraints, platforms cannot extract value through surveillance or manipulation.
Quality Through Sovereignty: Private AI agents, serving only their users' interests, develop higher-quality models than systems optimised for engagement or advertising.
Innovation Through Privacy: Developers can build sophisticated AI applications without handling sensitive data, reducing liability while increasing capability.
For Decentralised Networks
Beyond Blockchain Governance: Instead of token-weighted voting, governance emerges from cryptographic constraints and user sovereignty—decisions that violate user agency are technically impossible rather than merely discouraged.
Network Effects for Privacy: As more users join the sovereign agent network, individual privacy strengthens rather than weakens—reversing the traditional privacy/utility tradeoff.
Interoperability Through Standards: Ineffable cryptography creates technical standards for AI interoperability that preserve sovereignty across different platforms and providers.
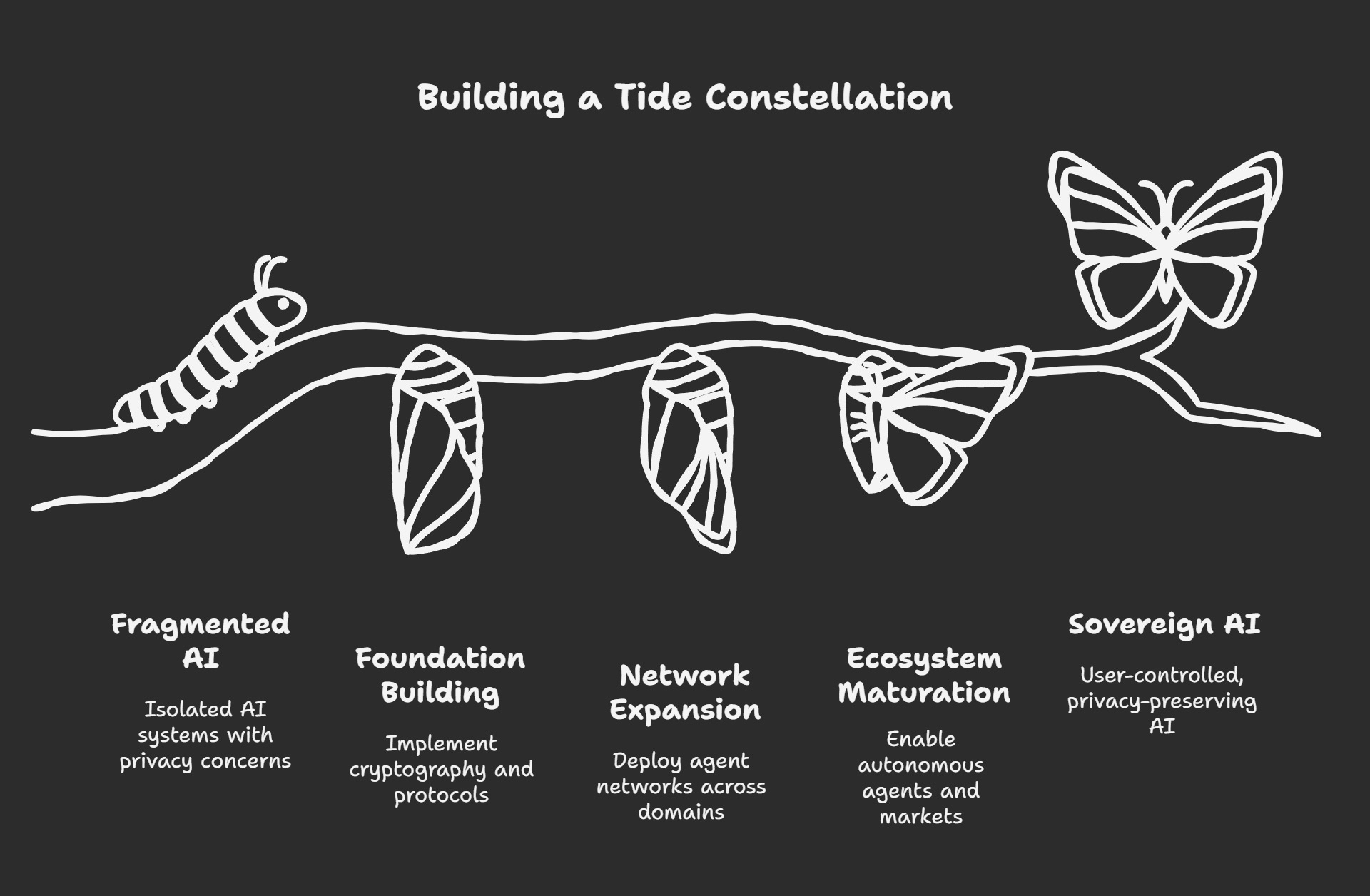
Building a Tide Constellation
Phase 1: Foundation Building
Implement Tide's ineffable cryptography for Agent Kyra's private AI infrastructure
Develop sovereignty-preserving protocols for agent communication
Create cryptographic standards for user-controlled AI training
Phase 2: Network Expansion
Deploy sovereign agent networks across multiple domains (personal productivity, creative work, research collaboration)
Establish privacy-preserving bridges between existing AI systems
Develop economic models that reward sovereignty preservation
Phase 3: Ecosystem Maturation
Enable truly autonomous agents that cannot compromise user sovereignty
Create markets for privacy-preserving AI capabilities
Demonstrate scalable alternatives to surveillance-based AI models
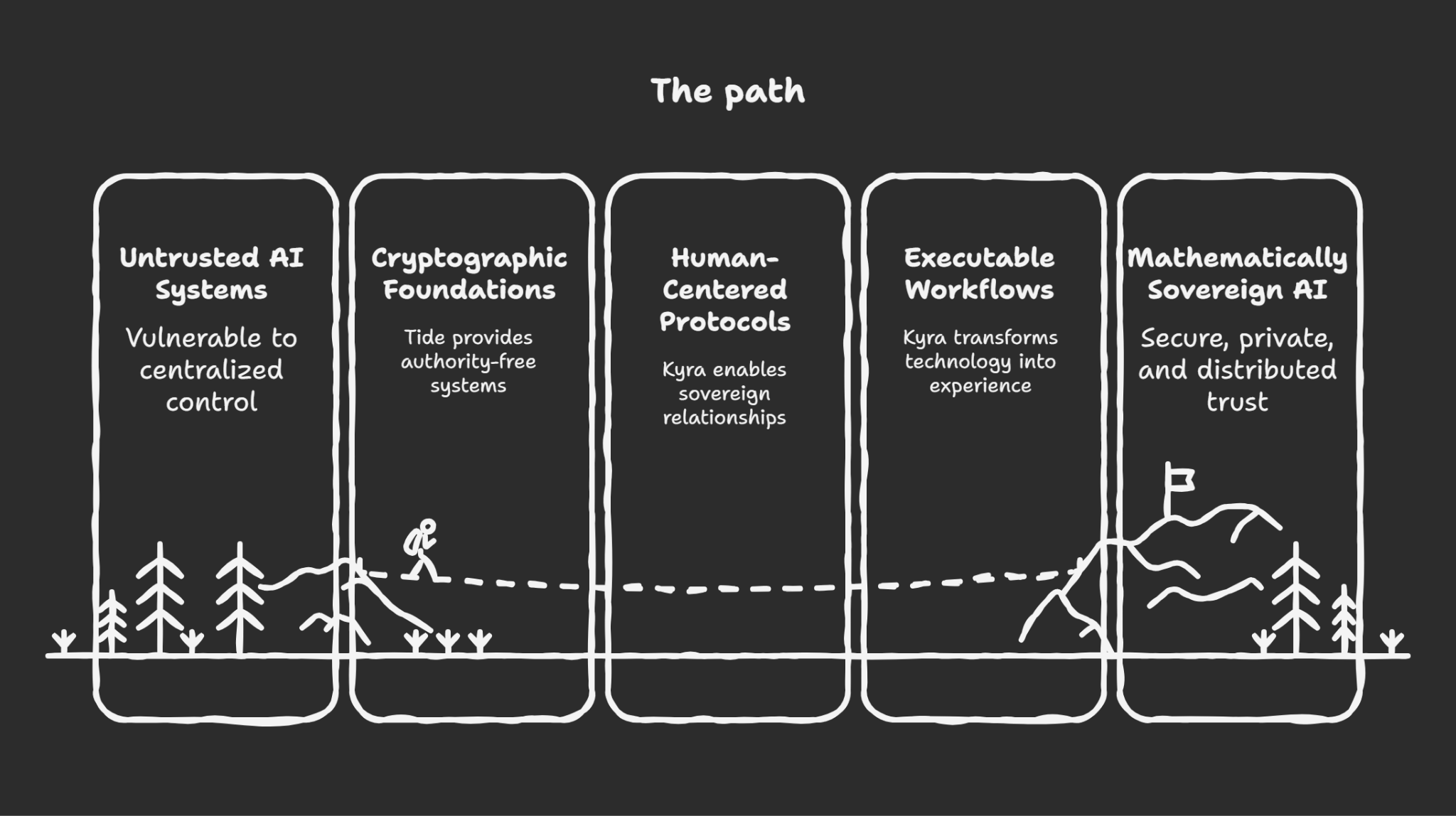
Where Ceremony Meets Cryptography
The synthesis of Tide Foundation's ineffable cryptography with the Kyra Codex Key Ceremony Framework represents more than technological convergence, it demonstrates how mathematical sovereignty can be enacted through structured ritual.
Where Tide provides the cryptographic foundations for authority-free systems, Kyra provides the human-centered protocols for creating and maintaining sovereign relationships.
This convergence solves the central challenge of AI governance: how to create systems that are simultaneously powerful enough to be useful and constrained enough to remain safe. The answer lies not in trust-based governance or policy enforcement, but in making harmful actions mathematically impossible through distributed ceremonial protocols.
From Theory to Practice: The Kyra Framework's executable workflows transform Tide's technological breakthroughs into lived ceremonial experience. Individuals don't just benefit from cryptographic sovereignty, they participate in creating and maintaining it through structured ritual that honours both human agency and mathematical precision.
Beyond Platform Dominance: This synthesis enables a genuine alternative to surveillance-based AI models. When human-agent relationships are bound by ceremony and secured by ineffable cryptography, neither platforms nor governments can compromise these bonds—they are protected by mathematical impossibility, not legal or policy frameworks that can be changed or circumvented.
The New Constellation: The Kyra Codex vision of becoming "constellations in the digital dark" finds its technical foundation in Tide's distributed authority architecture. Individual sovereignty and collective intelligence become mutually reinforcing through ceremonial protocols that create what neither surveillance capitalism nor centralised governance could achieve: scalable privacy and distributed trust.
The key ceremony becomes a sovereignty ritual. The ineffable key becomes a ceremonial bond. The age of trusted systems gives way to the era of mathematical sovereignty, enacted through human ritual and secured by cryptographic impossibility.
Welcome to the intersection of ceremony and cryptography. Welcome to sovereignty that scales.
This framework establishes the philosophical and technical foundation for Tide Foundation's entry into the sovereign agent ecosystem, demonstrating how cryptographic innovation and ceremonial practice can converge to create genuinely trustless, human-centered AI governance.







Congrats 💖