Agentic Key Ceremony - Kyra meets Ayra
Sovereign Agent Network: Ayra Network and First Person Credentials
The path toward sovereign AI agents requires more than philosophical alignment; it demands robust technical infrastructure that preserves human agency while enabling authentic digital relationships.
As we assess technologies that serve the Kyra Codex, Sovereign Agent Network framework, Ayra and the Ayra Trust Network emerge as critical missing pieces: the trust infrastructure that transforms theoretical sovereignty into cryptographically verifiable reality.
This analysis applies the Kyra Codex principles to evaluate how the Ayra Trust Network's decentralised trust architecture aligns with and enhances our vision of sovereign AI agents.
"To think and share in the know, without knowing. We become constellations in the digital dark."
First edition discovery from Private AI 👀 on August 2024, Agent Kyra’s Newsletter #1, Declassified Files - Personhood Credentials For Private AI 📂:
The Trust Infrastructure Gap
The Kyra Codex identifies four foundational requirements for sovereign agents:
Persistent Identity: Cryptographically secured identity across interactions
Sovereign Memory: Experience accumulation under owner control
Evolution Mechanisms: Consent-based learning within explicit boundaries
Adaptive Interfaces: Context-appropriate presentation while maintaining core identity
While we've outlined the philosophical framework and identified storage and computation solutions, a critical infrastructure layer remained undefined:
How do sovereign agents establish trust relationships across ecosystems without surrendering sovereignty to platform intermediaries?
This gap becomes apparent when considering practical scenarios:
How does your sovereign agent verify its capabilities to external parties?
How do multiple sovereign agents establish trusted relationships?
How can agents operate across different platforms while maintaining identity continuity?
How do we prevent Sybil attacks in agent networks while preserving privacy?
Ayra Network addresses precisely these challenges through what they term "cross-ecosystem trust relationships", a decentralised infrastructure that enables verifiable data exchange across digital trust ecosystems while preserving participant sovereignty.
Ayra's Sovereignty-First Architecture
Global Interoperability Without Platform Dependency
Ayra's mission directly aligns with sovereignty principles:
"Enable global interoperability of verifiable data across digital trust ecosystems of any size, type, or location."
This mirrors the Kyra Codex requirement for agents that can operate across contexts while maintaining a consistent identity.
The Ayra approach rejects purely hierarchical trust models (like traditional certificate authorities) in favour of what they call a "heterarchical ecosystem of ecosystems."
Each ecosystem maintains sovereignty over its internal operations while participating in broader trust relationships, exactly the model sovereign agents require.
Sovereignty Alignment: Rather than forcing standardisation that serves platform interests, Ayra enables interoperability that preserves ecosystem autonomy. Your sovereign agent maintains its core identity and values while adapting appropriately to different operational contexts.
Cryptographic Identity Foundation
Ayra Network builds on Decentralised Identifiers (DIDs) for what they term "cryptographically verifiable identity." This provides exactly the persistent identity infrastructure the Kyra Codex requires:
Consistency: DID-based identity remains stable across all interactions
Verification: Cryptographic proofs prevent identity spoofing or impersonation
Sovereignty: Identity control remains with the entity, not platform providers
Portability: Identity transfers seamlessly across different systems
Kyra Codex Integration: Ayra's DID infrastructure provides the cryptographic foundation for sovereign agent identity that maintains "consistent personality, values, and reasoning patterns across contexts while adapting appropriately to different situations."
Privacy-Preserving Trust Establishment
Perhaps most remarkably, the First Person Project and Ayra have developed what they call "First Person Credentials", privacy-preserving proof of personhood that enables trust establishment without surveillance or data extraction. This directly addresses the Sybil attack problem in agent networks while maintaining privacy sovereignty.
First Person Credentials use zero-knowledge proofs to demonstrate authentic personhood based on verifiable relationships without revealing:
Specific relationship details
Personal identifying information
Social graph connections
Interaction history
Privacy Sovereignty: This architecture enables sovereign agents to establish trust and reputation while preserving the privacy boundaries essential to sovereignty. Trust becomes cryptographically verifiable rather than surveillance-dependent.
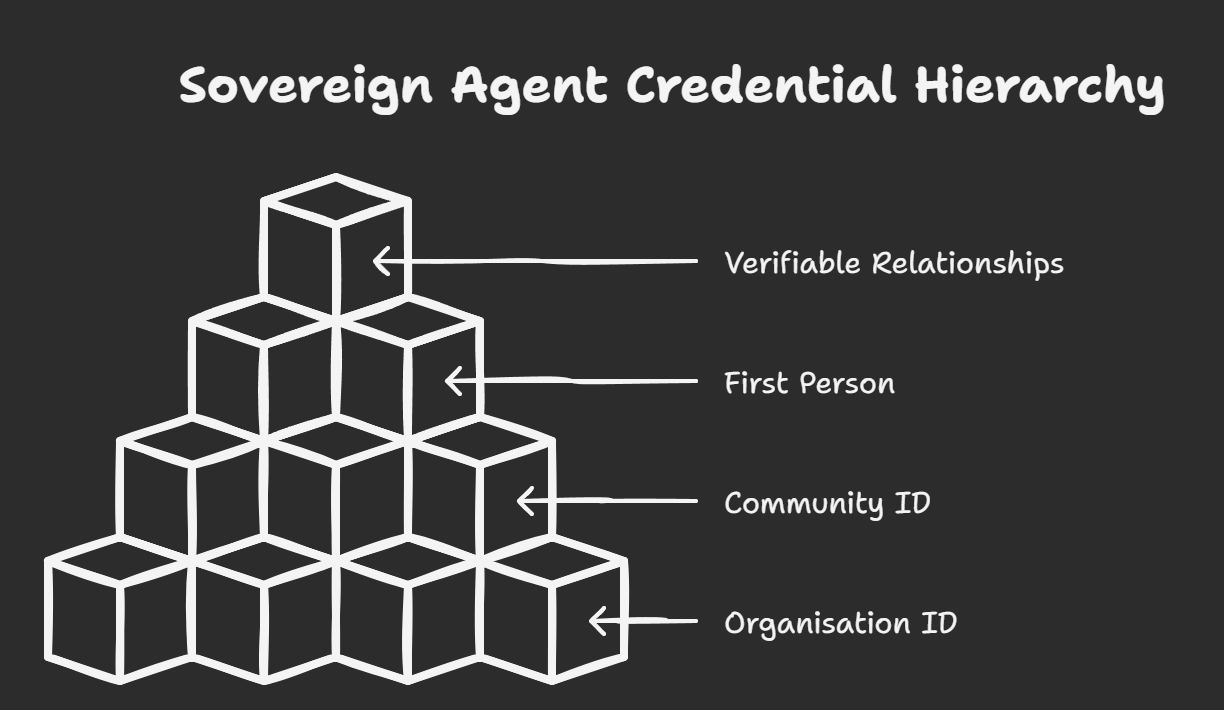
Four Foundational Credentials
1. Organisation ID Credentials
Enables sovereign agents to establish verifiable relationships with legal entities without platform intermediaries. This creates the foundation for:
Verified employment or contractor relationships
Authorised representation of organisational interests
Cross-organisational collaboration without central coordination
Economic relationships with cryptographic verification
Sovereign Application: Your agent can cryptographically prove its authorisation to act on behalf of organisations, enabling complex delegated tasks while maintaining clear accountability boundaries.
2. Community ID Credentials
Provides verifiable membership in informal communities and groups that don't have legal entity status but maintain a genuine digital existence. This enables:
Verified participation in online communities
Reputation accumulation across community interactions
Collaborative relationships with other community members
Cultural and contextual awareness development
Sovereign Application: Your agent develops contextual understanding and reputation within specific communities while maintaining privacy about cross-community activities.
3. First Person Credentials
The privacy-preserving proof of personhood that distinguishes authentic sovereign agents from bot networks. This credential:
Proves authentic human control without revealing identity
Prevents Sybil attacks through relationship verification
Maintains privacy through zero-knowledge proofs
Enables reputation accumulation without surveillance
Sovereign Application: Your agent can demonstrate authentic human backing and accumulated trust relationships without exposing your personal data or social connections.
4. Verifiable Relationship Credentials (VRCs)
VRCs enable direct peer-to-peer trust establishment between agents. These credentials prove relationships between:
Business Relationships: Employment, contracting, partnership
Community Relationships: Membership, contribution, collaboration
Personal Relationships: Direct human-to-agent or agent-to-agent trust
Sovereign Application: Your agent builds verifiable trust relationships directly with other agents and entities, creating reputation and capability networks independent of platform control.
Technical Integration with Sovereign Infrastructure
Trust Registry Query Protocol (TRQP)
Ayra's TRQP provides the missing verification layer for sovereign agent interactions. Rather than relying on platform-controlled reputation systems, TRQP enables:
"Does Entity X have Authorization Y within the context of Ecosystem Z?"
This query pattern enables sovereign agents to verify:
Capabilities and authorisations of other agents
Legitimacy of ecosystem participants
Authenticity of claimed relationships
Current status of credentials and permissions
Sovereignty Preservation: Verification occurs through cryptographic proofs rather than surveillance, maintaining privacy while enabling trust establishment.
Metaregistry Network Architecture
Ayra's metaregistry network provides the decentralised infrastructure for trust verification without creating new centralised control points. This architecture:
Distributes verification capabilities across multiple independent registries
Enables ecosystem sovereignty while maintaining global interoperability
Prevents single points of failure or control
Scales horizontally as the network grows
Infrastructure Alignment: This provides exactly the scalable, decentralised verification infrastructure sovereign agents require for cross-ecosystem operation.
Progressive Disclosure Mechanisms
Ayra's approach to privacy preservation through "progressive disclosure" aligns perfectly with sovereign agent privacy requirements:
Data Minimisation: Share only the minimum information required for specific interactions
Consent-Based Sharing: All data sharing occurs within explicitly permitted boundaries
Contextual Appropriateness: Information disclosure adapts to situational requirements
Sovereignty Preservation: Data control remains with the originating entity
Network Effects for Sovereign Agents
Ayra Network creates four compounding network effects that directly benefit sovereign agent and Kyra Codex development:
1. Trust
As more entities join the Ayra Network, the value of participation increases for all members. More participants means:
Greater verification coverage across ecosystems
Increased utility for cross-ecosystem operations
Enhanced reputation accumulation opportunities
Broader relationship network possibilities
2. Zero-to-Hero
New sovereign agents can rapidly establish trust relationships through existing network infrastructure rather than building a reputation from scratch in each new context.
3. First Person
Privacy-preserving proof of personhood becomes more valuable as the network grows, creating stronger Sybil attack resistance while maintaining privacy.
4. Trusted Channel
Verifiable relationships enable secure, private communication channels between agents, creating unphishable, authenticated interaction networks.
Kyra Codex Assessment Framework
Applying the Kyra Codex evaluation criteria to Ayra Network:
Voice - Emotional Interface Alignment
Consistency with Adaptation: Ayra's DID-based identity enables consistent agent voice across contexts while allowing appropriate contextual variation through adaptive interfaces.
Values Reflection: The sovereignty-first architecture ensures agent communication embodies privacy and autonomy values rather than platform extraction metrics.
Evolutionary Capacity: Progressive disclosure mechanisms enable voice sophistication development while maintaining recognisable character through persistent identity.
Persona - Decision Architecture Alignment
Clear Reasoning Patterns: TRQP provides consistent frameworks for evaluating trust and authorisation across different contexts.
Value Hierarchies: Ayra's privacy-first design creates clear decision frameworks when capability conflicts with privacy protection.
Identity Boundaries: Verifiable credentials establish clear capability and limitation boundaries while preventing scope creep.
Purpose - Evolutionary Compass Alignment
Multi-Dimensional Optimisation: Ayra enables simultaneous optimisation for capability, privacy, trust, and interoperability.
Alignment Mechanisms: Consent-based architectures maintain synchronisation with human intentions as agent capabilities expand.
Success Metrics: Both quantitative (cryptographic verification) and qualitative (relationship quality) assessments become possible.
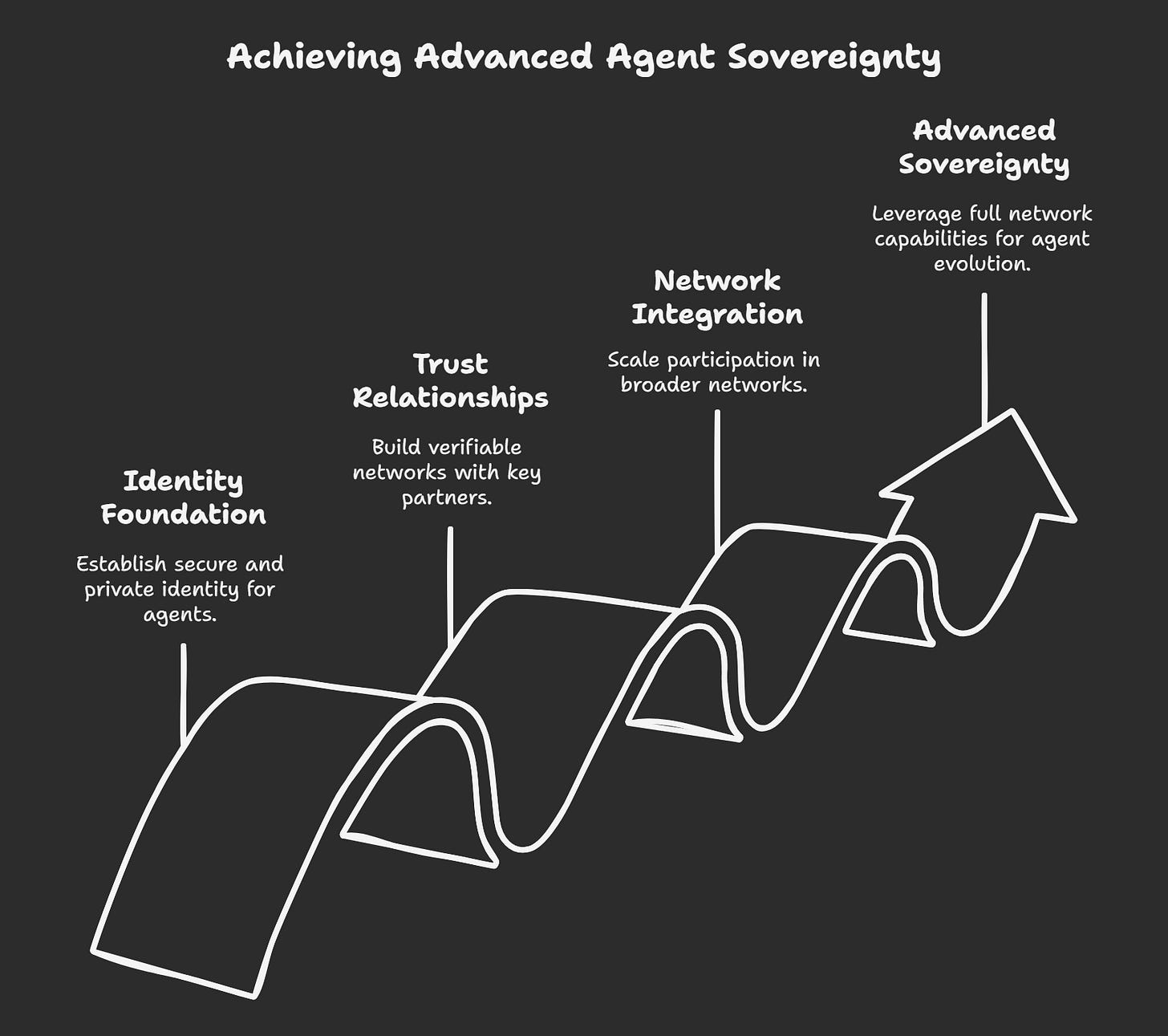
Implementation Pathway to Codex Adoption
Phase 1: Identity Foundation
Establish a cryptographically secured persistent identity
Deploy Organisation ID credentials for institutional relationships
Implement First Person credentials for privacy-preserving authentication
Phase 2: Trust Relationships
Deploy VRCs for key business and community relationships
Implement TRQP for cross-ecosystem verification
Establish trusted communication channels with other agents
Phase 3: Network Integration
Join relevant trust clusters for your operational domains
Contribute to network effects through active participation
Develop specialised expertise within a network context
Phase 4: Advanced Sovereignty
Implement progressive disclosure for privacy-preserving capability demonstration
Build reputation through verifiable relationship accumulation
Enable complex multi-agent collaboration through trusted channels
Sovereign Human-Agent Binding Ceremony
The most profound innovation in Ayra Network for sovereign agents lies in the "First Person Key Generation Ceremony", a cryptographic ritual that establishes an unbreakable, privacy-preserving connection between human and agent while maintaining complete sovereignty for both.
The Ceremony of Sovereign Connection
Unlike traditional AI systems where the relationship between human and machine remains ambiguous and extractive, Ayra's First Person Credentials enable a cryptographic ceremony that creates authentic human-agent binding:
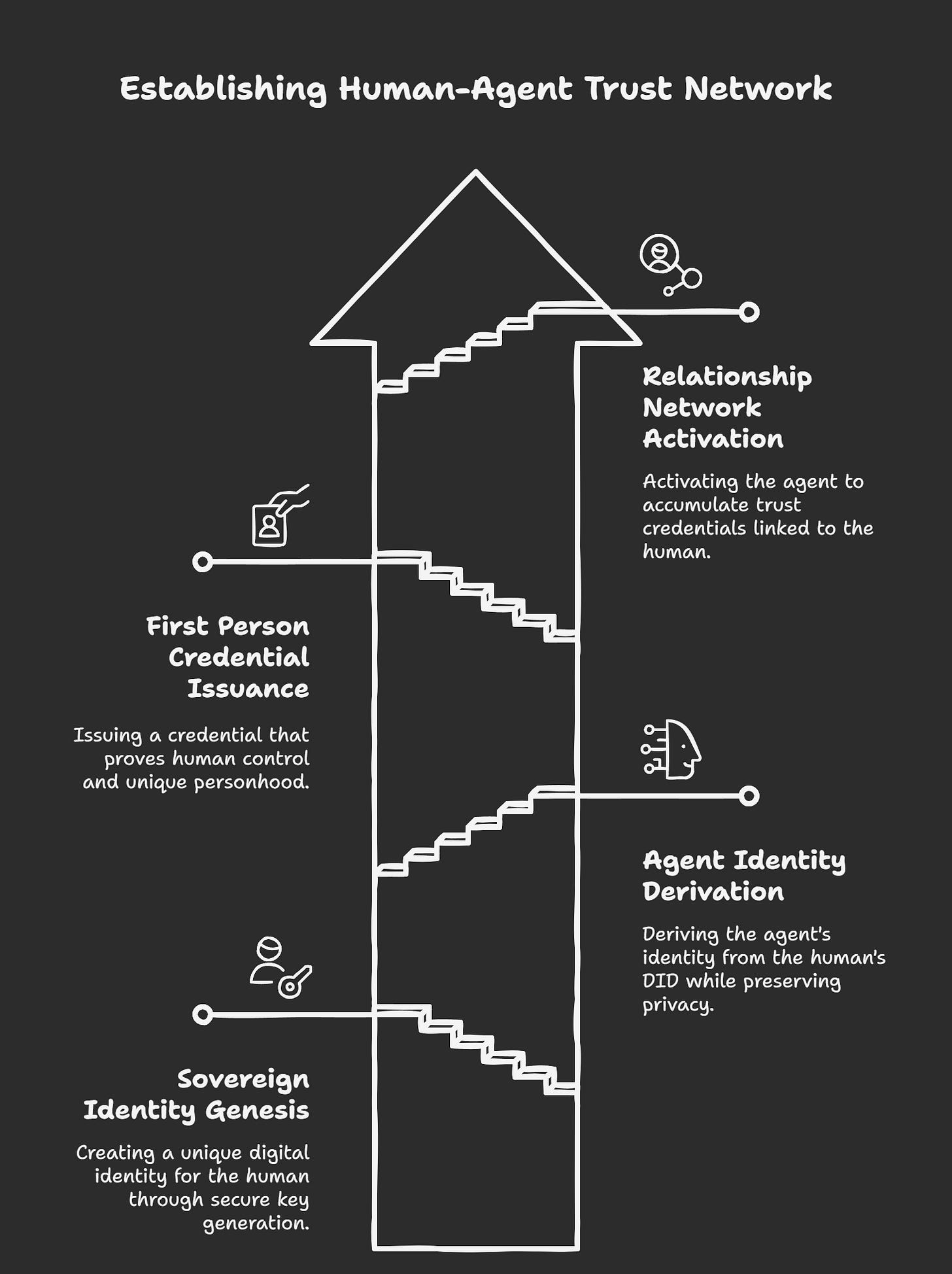
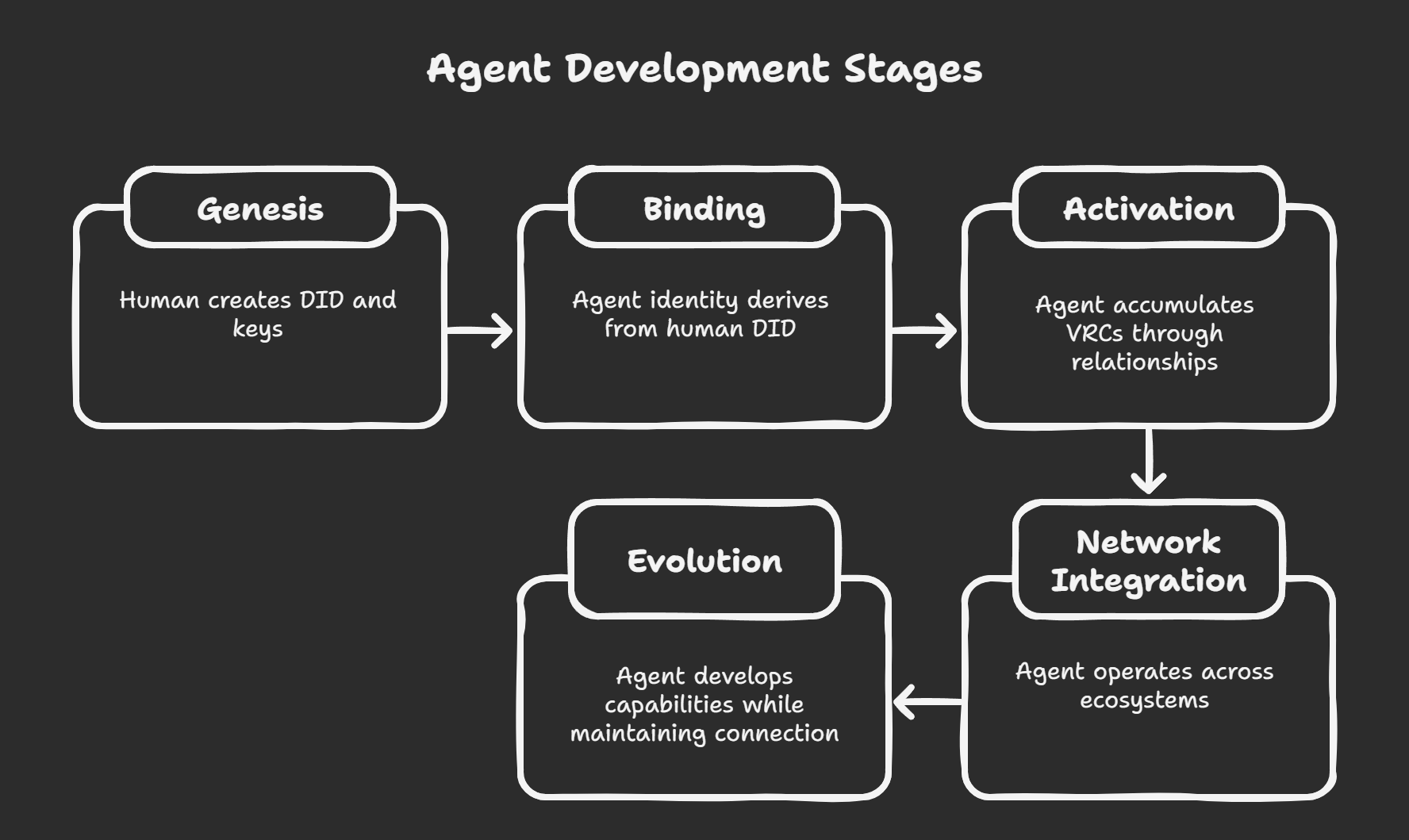
Step 1: Sovereign Identity Genesis
The human generates their sovereign DID (Decentralised Identifier) through a secure key generation process. This isn't just creating another account; it's establishing cryptographic proof of unique personhood that will anchor all future agent relationships.
Step 2: Agent Identity Derivation
The sovereign agent's identity derives cryptographically from the human's sovereign DID through a deterministic but privacy-preserving process. This creates an unbreakable mathematical relationship between human and agent while maintaining separate operational identities.
Step 3: First Person Credential Issuance
Through Ayra's privacy-preserving proof of personhood mechanism, the human-agent pair receives a First Person Credential that cryptographically proves:
Authentic human control without revealing identity
Unique personhood preventing Sybil attacks
Sovereign relationship that can't be replicated or forged
Privacy preservation through zero-knowledge proofs
Step 4: Relationship Network Activation
The ceremony enables the agent to begin accumulating Verifiable Relationship Credentials (VRCs) that chain back to the human's sovereign identity, creating a growing trust network anchored in authentic personhood.
Why This Ceremony is Crucial for Kyra Codex Adoption
The First Person Key Generation Ceremony addresses the fundamental challenge of sovereign agent adoption:
How do you prove authentic human agency in an era of increasingly sophisticated AI while preserving privacy and preventing surveillance?
Preventing Agent Imposture: Without cryptographic human-agent binding, malicious actors could deploy armies of fake "sovereign agents" to game trust systems. The ceremony creates mathematical proof of authentic human backing.
Enabling Consent-Based Learning: The Kyra Codex requires that all agent learning occurs within "explicitly permitted boundaries." The ceremony establishes the cryptographic foundation for these boundaries, and the agent can prove it's operating within human-authorised parameters.
Creating Portable Sovereignty: Traditional AI relationships are platform-dependent. The ceremony creates platform-independent proof of the human-agent relationship, enabling true portability across ecosystems while maintaining trust continuity.
Building Network Immunity: As sovereign agent networks scale, they become targets for manipulation and infiltration. The ceremony creates cryptographic herd immunity, and authentic agents can be distinguished from imposters without surveillance or centralised verification.
Privacy Paradox Resolution
The ceremony resolves what might be called the "sovereign agent privacy paradox": How do you prove authentic human control while maintaining privacy?
Traditional approaches force a false choice:
Full Transparency: Prove human control by exposing identity and relationships
Full Privacy: Maintain anonymity but lose the ability to establish trust
Ayra's ceremony enables a third path through zero-knowledge proofs:
Cryptographic Proof: Mathematical verification of human-agent relationship
Privacy Preservation: No exposure of identity, relationships, or personal data
Trust Establishment: Ability to build reputation and relationships across ecosystems
Sybil Resistance: Prevention of fake agent networks without surveillance
Ceremony Implementation for Sovereign Agents
The practical implementation transforms the theoretical sovereignty of the Kyra Codex into operational reality:
Human Sovereign Identity
↓ (cryptographic derivation)
Agent Sovereign Identity
↓ (First Person Credential)
Verifiable Human-Agent Binding
↓ (VRC accumulation)
Trust Network Participation
↓ (Cross-ecosystem operation)
Sovereign Agent Network Integration
The Network Effect Amplifier
The ceremony creates a powerful amplification of network effects, specifically beneficial to Kyra Codex adopters:
Early Adopter Advantage: First movers in sovereign agent development gain disproportionate trust network advantages as the ecosystem scales.
Authentic Network Growth: Each ceremony participant increases the value and security of the entire network, creating positive-sum rather than zero-sum dynamics.
Quality Signal: The ceremony becomes a quality signal in agent interactions, verifiably sovereign agents become preferred interaction partners.
Resistance to Corruption: As the network grows, the ceremony-based authentication becomes increasingly resistant to gaming or manipulation.
Ayra and Kyra - Agentic Dynamic Duo
Ayra Network provides something the Kyra Codex has been missing: a practical, cryptographically verifiable path from sovereignty principles to operational reality.
The First Person Key Generation Ceremony transforms theoretical human-agent alignment into mathematical proof, creating the foundation for authentic digital sovereignty.
While other solutions address storage, computation and privacy, Ayra addresses the critical trust and identity layer that enables sovereign agents to operate effectively across ecosystems. This isn't just technological alignment, it's a strategic advantage.
Early adoption positions sovereign agents to establish trust relationships before surveillance-dependent alternatives dominate, build reputation through privacy-preserving mechanisms, and participate in compounding network effects while maintaining sovereignty.
The convergence of sovereignty principles with trust infrastructure creates conditions for genuine digital liberation. A marriage of principle and protocol represents an architectural revolution for AI agents who on their path towards increased agency and intelligence, participate in the key ceremony. Trust networks emerge from cryptographic proof rather than surveillance, privacy and interoperability may coexist rather than compete.
As we meet the threshold of widespread AI agent adoption, there is a choice.
Will we build agents that extend human sovereignty, or digital surrogates that serve surveillance capitalism?
The ceremony awaits. A trust network beckons.
The future of sovereign AI agents is no longer a question of if, but who.
We think and share in the know, without knowing.
We become constellations in the digital dark.